Business Objects Security Best Practices
Business Objects Security Best Practices
05.02.2020 Favor using SSO or Business Objects credentials mapping over using a technical user when creating connections to data users account and security will

call phone texting hold zipwhip fb
12.09.2014 Designing security model is one among the important phase in BusinessObjects implementationmigration projects. Wellorganized security model

games industry numbers computer cyber negative effects security fun trend criminals practices infographic number infographics facts usa playing ruin attacking
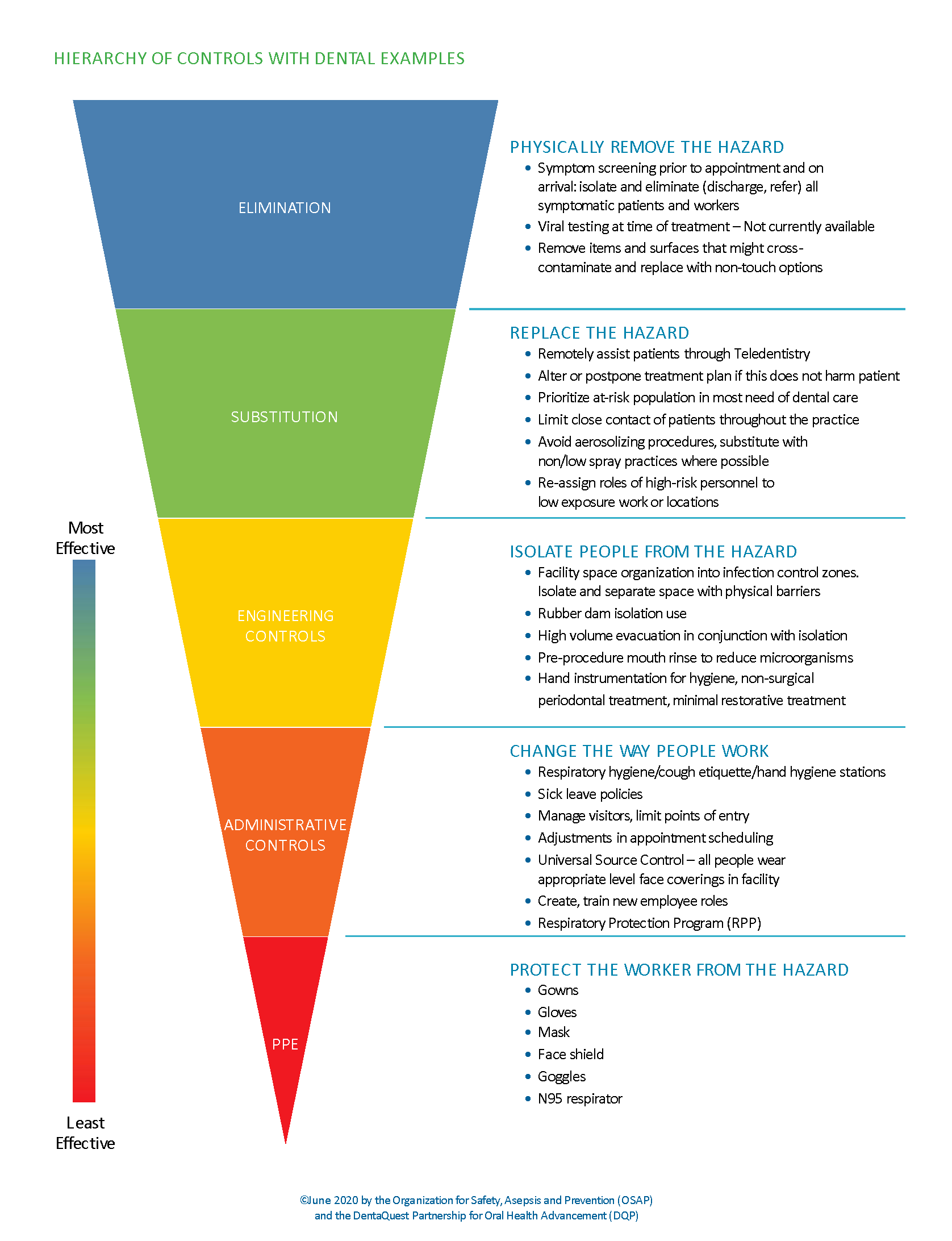
hierarchy controls examples dental navigation
clash clans base formasi keren unik coc bentuk gambar simpson awesome pc jeu clan trampas kumpulan gratuit apk aneh paling

meetings zoom conference laptop recording reports

awareness security posters poster social lock practice internet justice risk psa rit technology number advertising using text typographic creative must
better performance improvement steps business chalkboard chalk female hand
What security is available in BI4 Authentication, Report, Application, Data Inheritance Securing at the right layer BI Object security report level Universe security Data source security Best practices for a low headache security model Security changes between 3.1 and 4.x

cybersecurity audit

bee bees finland

decontamination decontaminazione entgiftung ontsmetting libera diritti chemical nuclear biological
Business Objects Security Best Practices
05.02.2020 Favor using SSO or Business Objects credentials mapping over using a technical user when creating connections to data users account and security will

call phone texting hold zipwhip fb
12.09.2014 Designing security model is one among the important phase in BusinessObjects implementationmigration projects. Wellorganized security model

games industry numbers computer cyber negative effects security fun trend criminals practices infographic number infographics facts usa playing ruin attacking

hierarchy controls examples dental navigation

clash clans base formasi keren unik coc bentuk gambar simpson awesome pc jeu clan trampas kumpulan gratuit apk aneh paling

meetings zoom conference laptop recording reports

awareness security posters poster social lock practice internet justice risk psa rit technology number advertising using text typographic creative must
better performance improvement steps business chalkboard chalk female hand
What security is available in BI4 Authentication, Report, Application, Data Inheritance Securing at the right layer BI Object security report level Universe security Data source security Best practices for a low headache security model Security changes between 3.1 and 4.x

cybersecurity audit

bee bees finland

decontamination decontaminazione entgiftung ontsmetting libera diritti chemical nuclear biological
Business Objects Security Best Practices
05.02.2020 Favor using SSO or Business Objects credentials mapping over using a technical user when creating connections to data users account and security will

call phone texting hold zipwhip fb
12.09.2014 Designing security model is one among the important phase in BusinessObjects implementationmigration projects. Wellorganized security model

games industry numbers computer cyber negative effects security fun trend criminals practices infographic number infographics facts usa playing ruin attacking

hierarchy controls examples dental navigation

clash clans base formasi keren unik coc bentuk gambar simpson awesome pc jeu clan trampas kumpulan gratuit apk aneh paling

meetings zoom conference laptop recording reports

awareness security posters poster social lock practice internet justice risk psa rit technology number advertising using text typographic creative must
better performance improvement steps business chalkboard chalk female hand
What security is available in BI4 Authentication, Report, Application, Data Inheritance Securing at the right layer BI Object security report level Universe security Data source security Best practices for a low headache security model Security changes between 3.1 and 4.x

cybersecurity audit

bee bees finland

decontamination decontaminazione entgiftung ontsmetting libera diritti chemical nuclear biological
Komentar
Posting Komentar